Zoom is making some drastic changes to prevent rampant abuse as trolls attack publicly-shared video calls. Starting April 5th, it will require passwords to enter calls via Meeting ID, since these may be guessed or reused. Meanwhile, it will change virtual waiting rooms to be on by default so hosts have to manually admit attendees.
The changes could prevent “Zoombombing”, a term I coined two weeks ago to describe malicious actors entering Zoom calls and disrupting them by screensharing offensive imagery. New Zoombombing tactics have since emerged, like spamming the chat thread with terrible GIFs, using virtual backgrounds to spread hateful messages, or just screaming profanities and slurs. Anonymous forums have now become breeding grounds for organized trolling efforts to raid calls.
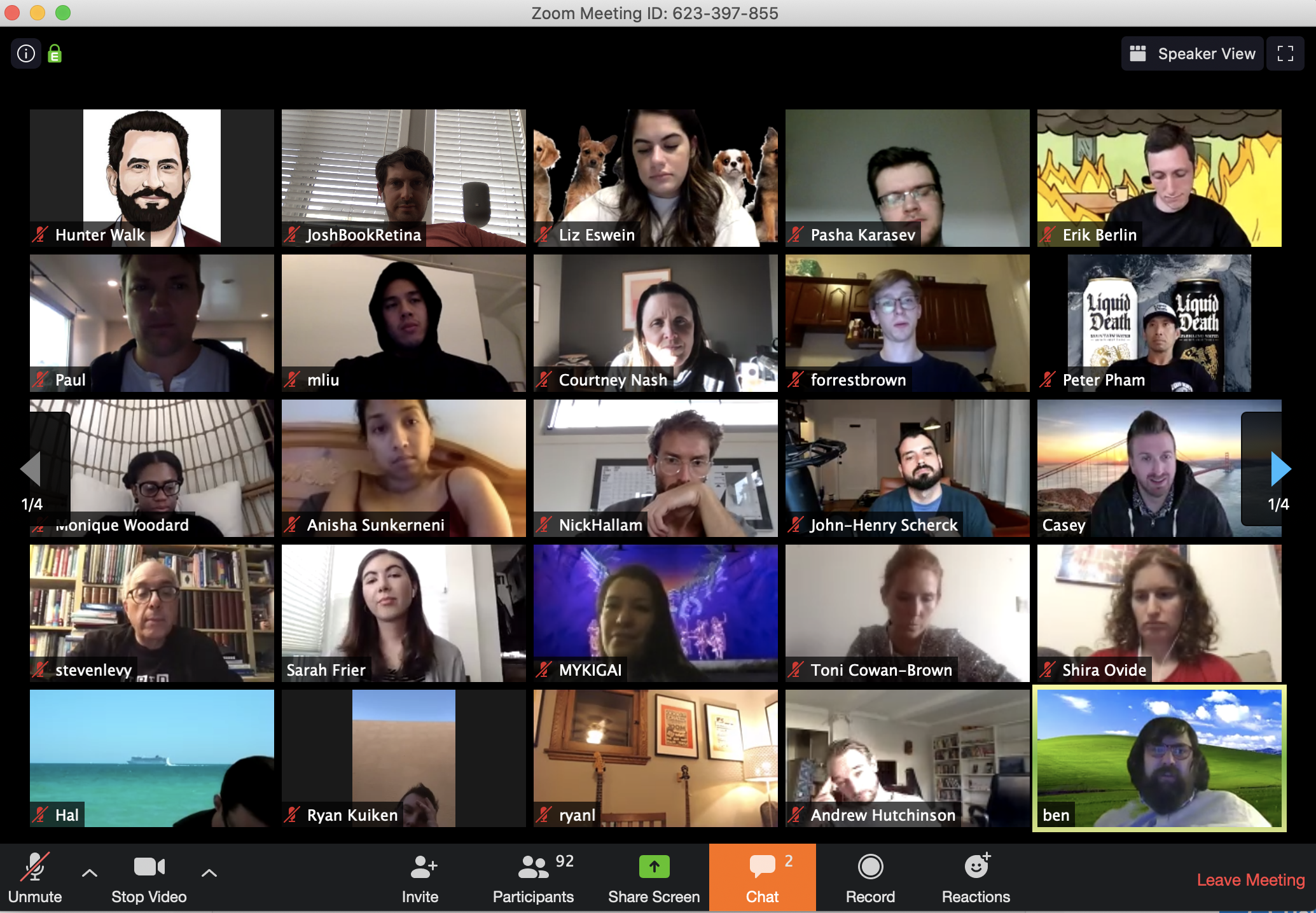
Just imagine the most frightened look on all these people’s faces. That’s what happened when Zoombombers attacked the call.
The FBI has issued a warning about the Zoombombing problem after children’s online classes, alcoholics anonymous meetings, and private business calls were invaded by trolls. Security researchers have revealed many ways that attackers can infiltrate a call.
The problems stem from Zoom being designed for trusted enterprise use cases rather than cocktail hours, yoga classes, roundtable discussions, and classes. But with Zoom struggling to scale its infrastructure as its daily user count has shot up from 10 million to 200 million over the past month due to coronavirus shelter-in-place orders, it’s found itself caught off guard.
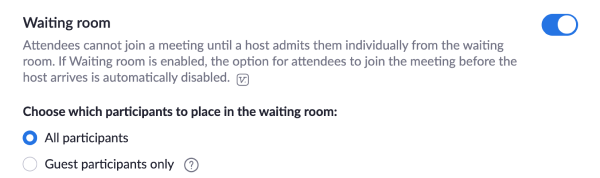
Zoom CEO Eric Yuan apologized for the security failures this week and vowed changes. But at the time, the company merely said it would default to making screensharing host-only and keeping waiting rooms on for its K-12 education users. Clearly it determined that wasn’t sufficient, so now waiting rooms are on by default for everyone.
Zoom communicated the changes to users via an email sent this afternoon that explains “we’ve chosen to enable passwords on your meetings and turn on Waiting Rooms by default as additional security enhancements to protect your privacy.”
The company also explained that “For meetings scheduled moving forward, the meeting password can be found in the invitation. For instant meetings, the password will be displayed in the Zoom client. The password can also be found in the meeting join URL.” Some other precautions users can take include disabling file transfer, screensharing, or rejoining by removed attendees.

NEW YORK, NY – APRIL 18: Zoom founder Eric Yuan reacts at the Nasdaq opening bell ceremony on April 18, 2019 in New York City. The video-conferencing software company announced it’s IPO priced at $36 per share, at an estimated value of $9.2 billion. (Photo by Kena Betancur/Getty Images)
The shift could cause some hassle for users. Hosts will be distracted by having to approve attendees out of the waiting room while they’re trying to lead calls. Zoom recommends users resend invites with passwords attached for Meeting ID-based calls scheduled for after April 5th. Scrambling to find passwords could make people late to calls.
But that’s a reasonable price to pay to keep people from being scarred by Zoombombing attacks. The rash of trolling threatened to sour many people’s early experiences with the video chat platform just as it’s been having its breakout moment. A single call marred by disturbing pornography can leave a stronger impression than 100 peaceful ones with friends and colleagues. The old settings made sense when it was merely an enterprise product, but it needed to embrace its own change of identity as it becomes a fundamental utility for everyone.
Technologists will need to grow better at anticipating worst-case scenarios as their products go mainstream and are adapted to new use cases. Assuming everyone will have the best intentions ignores the reality of human nature. There’s always someone looking to generate a profit, score power, or cause chaos from even the smallest opportunity. Building development teams that include skeptics and realists, rather than just visionary idealists, could keep ensure products get safeguarded from abuse before rather than after a scandal occurs.
from Social – TechCrunch https://ift.tt/3bNbbW8
No comments:
Post a Comment